All of a sudden, one fine morning we received a notification from our G8keeper application that there was a surge in CPU usage on a server. This server is a low traffic WordPress blog and no marketing campaign was planned so this surge was completely unexpected and called for deeper investigation. It is in times like these the G8keeper application comes in very handy. G8keeper keeps track most of the vital server statistics that makes any such investigation very simple.
Looking at the G8keeper dashboard, it was evident that the surge in traffic was due to CPU Steal on the server. However, on deeper investigation, by looking at the processes running and consuming substantial CPU, Apache was identified at the process causing the surge.
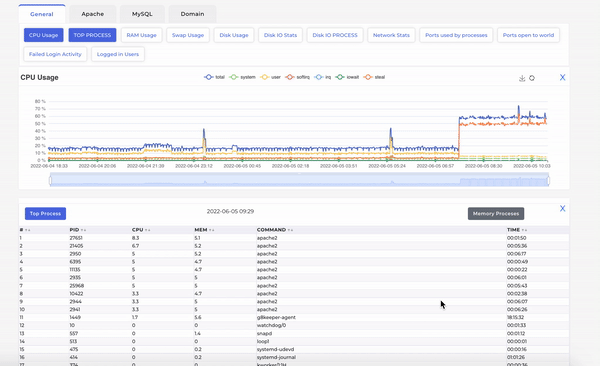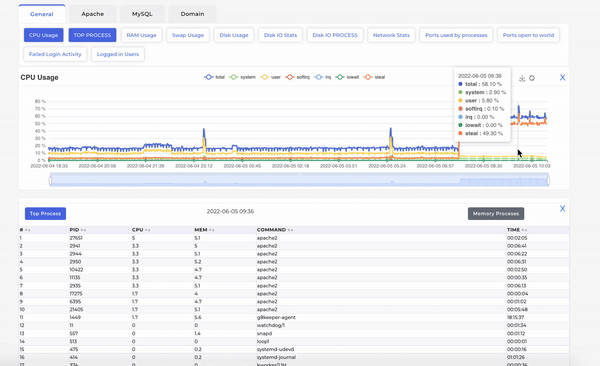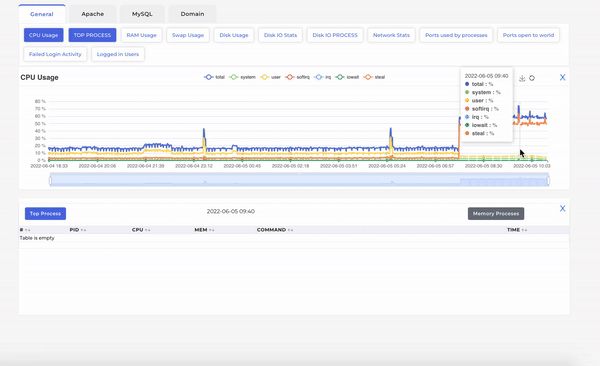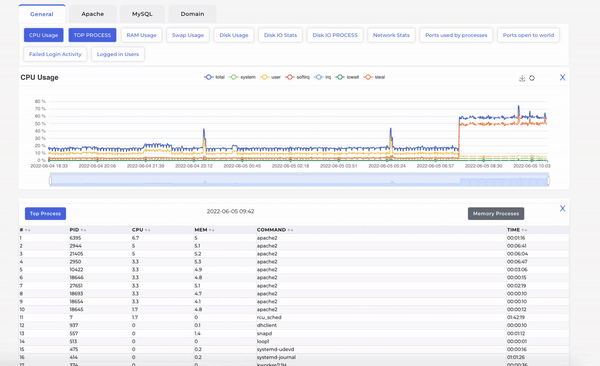
As can be seen above, when we move mouse on the CPU timeline, the processes running on server at that time are displayed with their respective CPU consumption etc.
Once Apache was identified, we wanted to further investigate the traffic on Apache. Which can also be easily done by adding the Apache traffic widget.
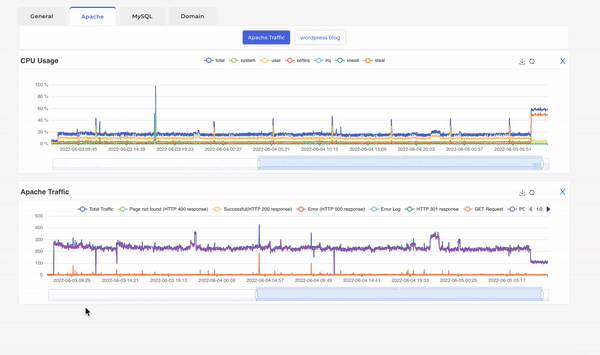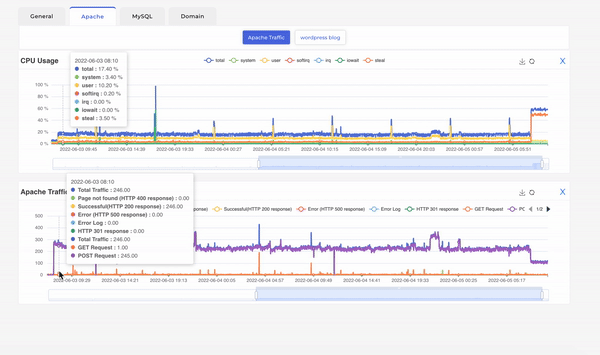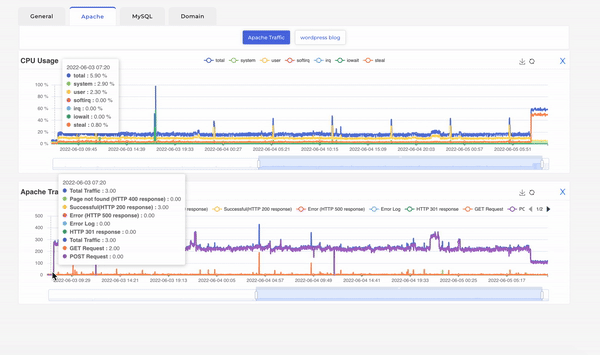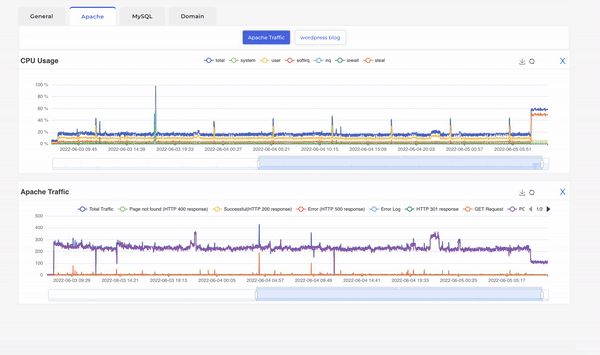
Looking at the apache traffic alongside CPU usage we can see that the surge in traffic due to apache itself as it directly corelates to the same. Also, we can see the surge in Apache traffic is entirely due to web POST requests. Web POST requests are mostly used to submit data on forms in website and you should not see such high number POST / GET request ratio that we see in this scenario which was approximately 250 to 5. This finding prompted us to look at apache server logs and voila! Someone was trying to bruteforce login into our wordpress blog using xmlrpc.php.
Since we were not using any RPC on our WordPress instance, we disabled the file and traffic, and CPU usage was back to normal. We did some more investigation using G8keeper’s File Integrity Monitoring to ensure none of the files / folders were modified on the server in last few days to ensure that WordPress instance on the server was not hacked.